Cybersecurity is indispensable when it comes to protecting digital assets like data and networks against fraudulent activities. It first emerged commercially in 1987 and today is a mainstream component of business risk management strategy. Over the years, there has been a paradigm shift in the cybersecurity landscape as it evolved from a mere concept to successfully predicting and mitigating threat vectors.
The cybersecurity market is poised to reach $562.72 billion by 2032 from $193.73 billion in 2024 at a 14.3% CAGR. In short, it is one of the most in-demand areas of today’s digital ecosystem since a single breach can damage safety and reputation and put businesses behind competitors. Now at this point, you must be wondering how to make sure your security measures are working? Especially since it is not a one-time affair and demands continuous tracking and monitoring of cybersecurity KPIs for businesses.
Read on to get a clear idea for better decision-making.
Table of contents
What are cybersecurity metrics and KPIs?
In simple terms, these are a multitude of measurements that are in place to analyze the effectiveness of a business’ efforts to stay safe against cybercrime. However, cybersecurity metrics and KPIs are different. Let’s understand:
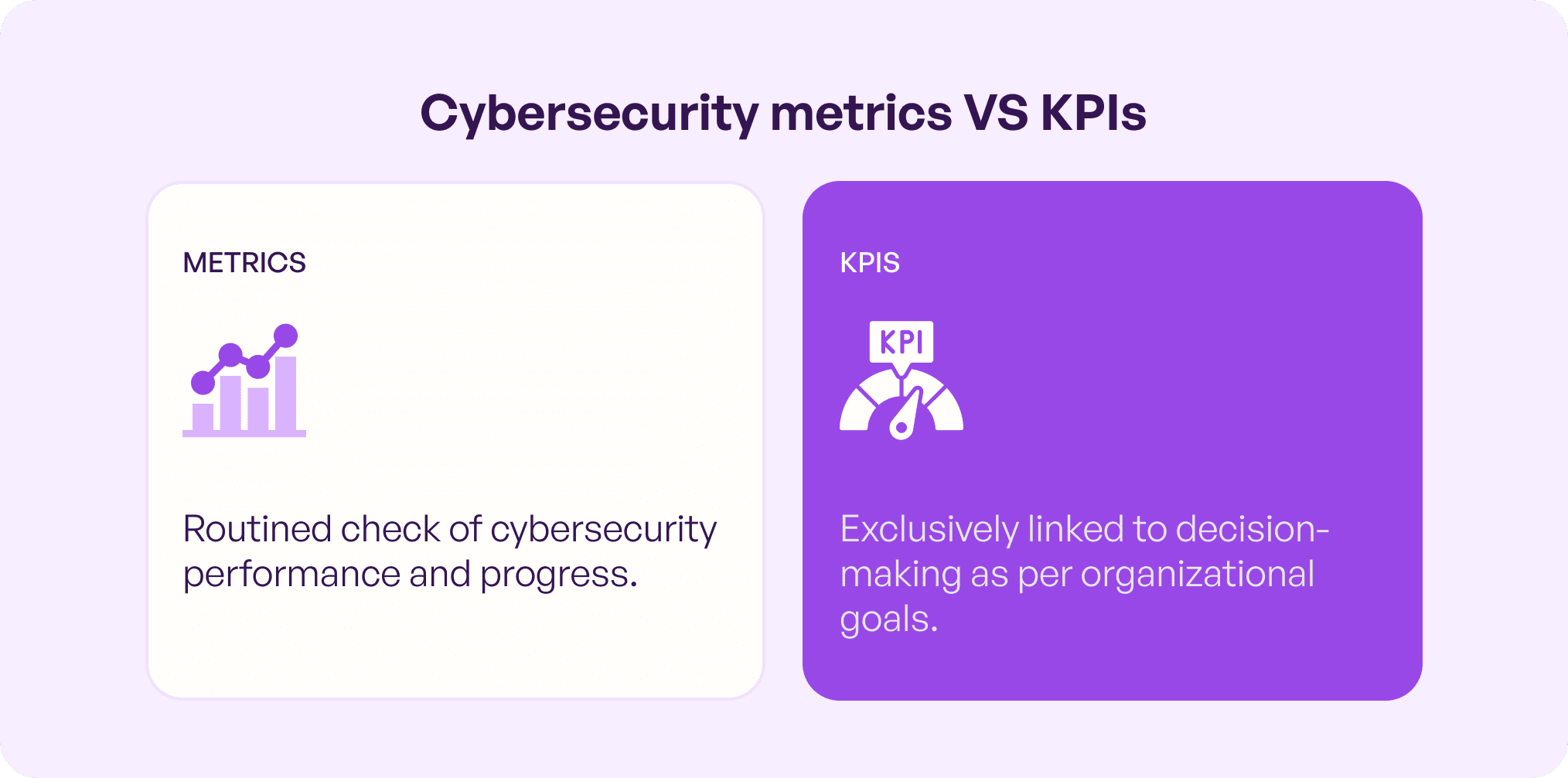 Metrics: These are bits and pieces of information that an organization uses on a daily basis with the help of specific tools. It helps them justify their progress towards establishing a robust security system. There are 4 main types of metrics
Metrics: These are bits and pieces of information that an organization uses on a daily basis with the help of specific tools. It helps them justify their progress towards establishing a robust security system. There are 4 main types of metrics
- Vulnerability assessment metrics : open systems and unpatched ports.
- Compliance metrics: security policies and controls.
- Attack detection and prevention metrics: MTD/R and prevented attacks.
- Performance metrics: number of security incidents and their costs.
KPIs: Key Performance Indicators are any parameters that have a direct impact on the decision-making process of an organization. Now, KPIs for cybersecurity specifically refers to measurable values that reflect how well your business is achieving its security goals and objectives thus ultimately gaining competitive advantage.
Why do we need cybersecurity KPIs?
Cyberthreats are on the rise like never before since criminals today use advanced skills and sophisticated techniques. Owing to this, the cybersecurity market size stood at $182.84 billion in 2024 and is poised to reach $314.28 billion by 2029 growing at 11.4% CAGR. These statistics are a fair proof that cyberthreats are proliferating and data-intensive approaches are of primary importance. So, businesses undoubtedly must prioritize security by measuring KPIs to stay ahead and avoid operations disruptions.
To do the same, consider collaborating with cybersecurity experts at Simublade rated 5 star on GoodFirms based on our services and client satisfaction in terms of mobile app development. Our world class firm offers intrusion detection and prevention, vulnerability scanning, data encryption, network monitoring, security patch management, incidence response, and penetration testing. These are a necessity for both established businesses and startups in this digital age to protect their data from getting breached.
Important cybersecurity KPIs for businesses
In cyber security context, KPIs are effective ways to measure the success of cybersecurity programs by offering the necessary data to understand if any business or organization is exposed to risk. Lets see a few ways regarding how to measure cybersecurity KPIs.
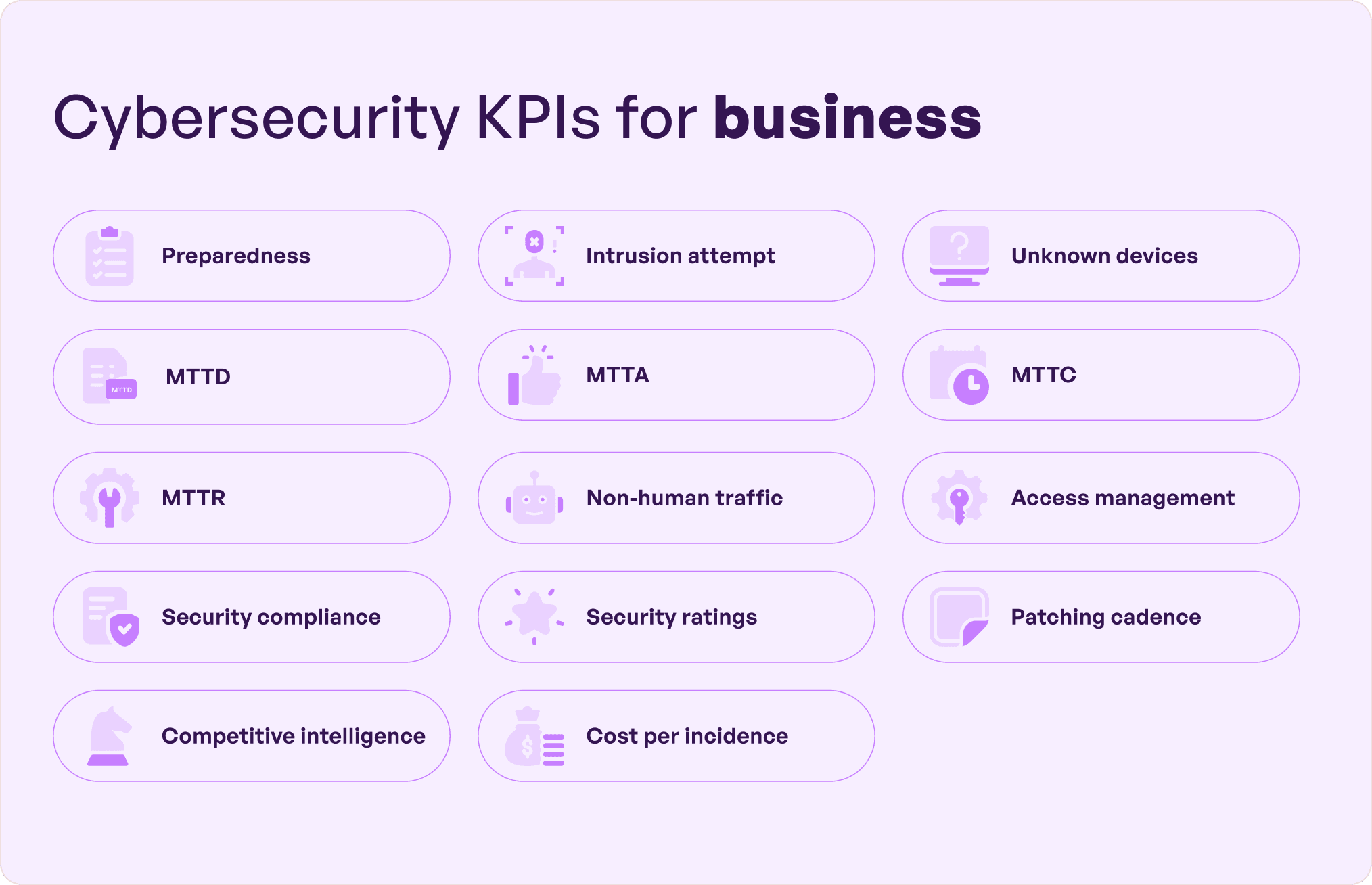
1. Preparedness
This is a core KPI that measures how well-prepared your organization is to handle attacks and ultimately come up with an accurate solution. For this, you need to review your response strategies and security infrastructure like devices and networks and see if they are up-to-date and completely patched. Further, make sure to do the following at regular intervals :
- identify high-risk vulnerabilities and end-of-life software
- test phishing susceptibilities, simulations and business continuity plans
- allocate special resources to manage critical threats
- analyze fishy behavior and patterns to predict the future moves
- track the percentage of devices for frequent backups
- conduct classification and retention policies
- make data-driven decisions when it comes to security issues
Altogether, these cybersecurity strategies maintain a robust defense against potential attacks and increase the overall value of your risk management program.
2. Intrusion attempt
Intrusion attempts should be tracked continuously, for instance, regular review of firewall logs to check for unauthorized access that might target organizations. This is one of the topmost cybersecurity measurement metrics that can be helpful to detect and block cybercrime from network traffic. Further, collaborating with experts can also help detect false positives and false negatives in the detection system, help with source identification, and data loss prevention. Altogether, this helps with fine-tuning safety protocols and adjusting security controls.
3. Presence of unknown devices
IoT devices in the internal network could be a risky affair for your organizational security. In fact, studies have shown that routers comprise 75% of infected IoT devices since they offer access to nodes on a network and remain a top concern for businesses in 2024. Additionally, personal systems of employees on an organizational network are likely to pose a threat and turn into entry points for cyber intruders.
The best way to tackle these is to partner with us at Simublade. We ensure 360° protection assurance by building a system that can proactively spot a hack instance even before your business is compromised. Our cybersecurity services include vulnerability management, cloud migration, disaster recovery plan, multi-factor authentication, and endpoint detection and response. We offer startups and enterprise cybersecurity solutions that range between $20K to $50K to cater to all kinds of budget preferences without compromising the quality of our work.
Next is a list of cybersecurity metrics and KPIs that are time-focused when it comes to analyzing specific aspects of a threat. This makes it fundamental to benchmark your strategies with the industry standards, pinpoint security gaps in the business, and fill them. Find out below:
4. Mean-time-to-detect (MTTD)
It is the average duration that a cybersecurity team takes to detect a breach. Therefore, this KPI is extremely critical to assess the responsiveness of your protection strategies. This step is necessary since a study of 79,000 breaches across 88 countries found that 20% of incidents took months or more to be just discovered.
5. Mean-time-to-acknowledge (MTTA)
It is the average duration between the initial threat detection and the time taken to formally register it. So, it is vital to standardize MTTA to ensure quick actions instead of delayed handling of the cybersecurity issues. The process can include optimizing communication channels and refining alert measures to stay safe.
6. Mean-time-to-contain (MTTC)
It indicates the efficacy with which the cybersecurity professionals will mitigate the risks when they are identified. This also includes the time taken to do so, which means, how swiftly they could implement containment strategies. Further, keeping this KPI in check also helps receive insights into security loopholes that require improvements like awareness training and procedure updates.
7. Mean-time-to-resolve (MTTR)
It is the average duration that a cybersecurity team actually takes to efficiently recover from a security incident. Further, it helps to identify how effective are the recovery processes, protocols, and improvements to help strengthen cybersecurity resilience. The aim must be to reduce the MTTR to be able to boost response abilities.
8. Non-human traffic (NHT)
A sudden uptick in website traffic is typical of a bot attack created by spiders and programs which show misleading data and impacts business performance. This has become quite common, here’s why. The 2024 Imperva Threat Research report states that 50% of internet traffic is made up of non-human sources. So, a bot management solution must be in place to ensure malicious bots are not able to reach your website and conduct attacks like stealing information or creating phishing accounts.
9. Access management
This cybersecurity KPI for businesses measures the authenticity of user access to business networks like:
- how sensitive data is controlled
- the frequency of auditing user accounts
- whether multi-factor authentication is in place
- how secure access practices are being promoted
- which tools are being used to review user activities
Additionally, this cybersecurity strategy also establishes the limitations of user access and ways to prevent escalation attacks along with documenting them in detail.
10. Security compliance
It must be an organization’s utmost priority to ensure that their preventive actions are in sync with industry-specific standards of cybersecurity like PCI-DSS, GDPR, and HIPAA.
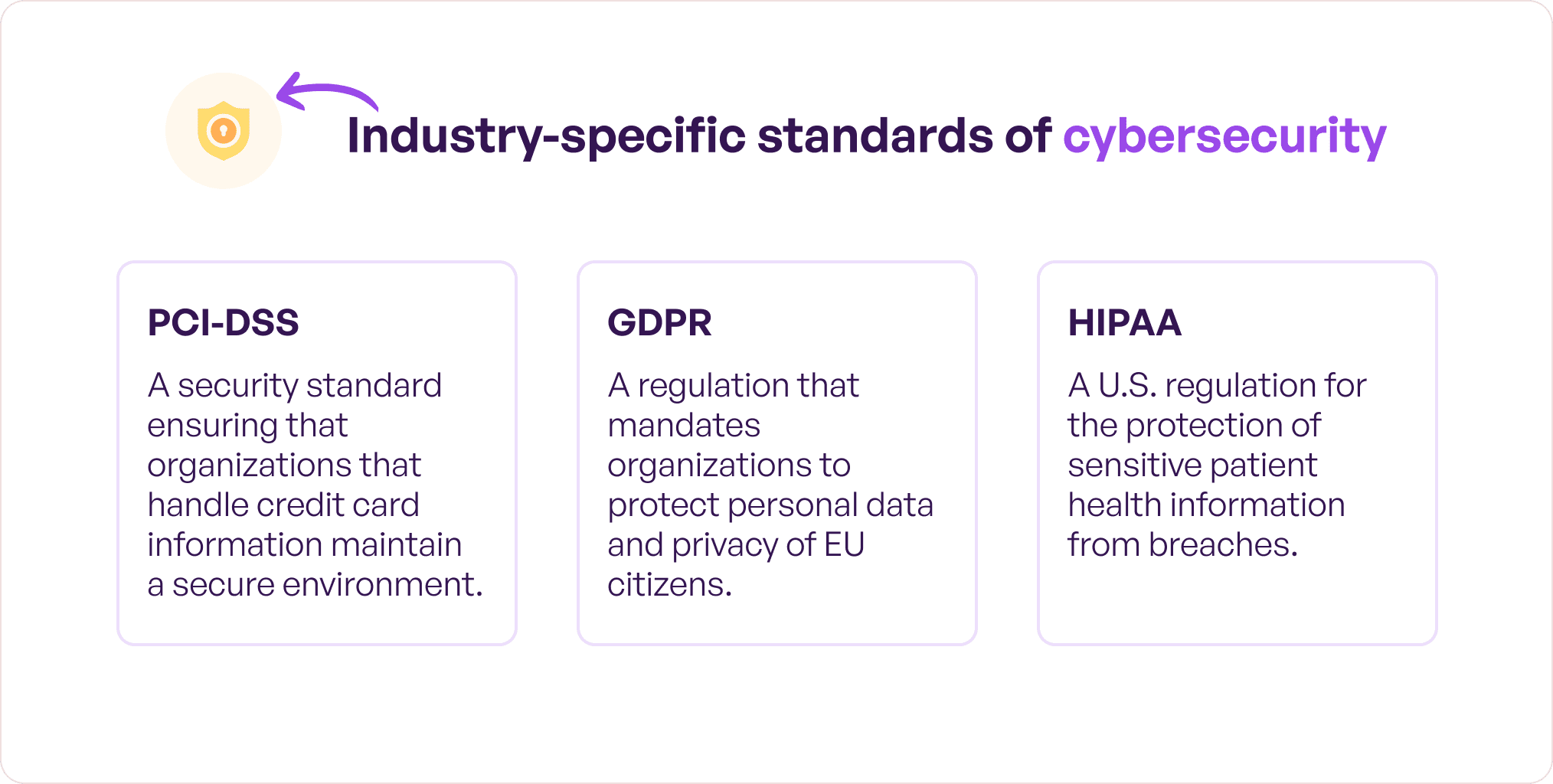 These compliance must be monitored regularly and restrictions must be enforced in case of any illegal activities. Also, exceptions must be tracked and documented to help secure business data and the overall operations in general.
These compliance must be monitored regularly and restrictions must be enforced in case of any illegal activities. Also, exceptions must be tracked and documented to help secure business data and the overall operations in general.
11. Security ratings
Communicating cybersecurity parameters to non-technical employees of the organization is a mandate to help them understand the seriousness of risks. Businesses can consider using A-F letter grades on at least 10 or more security categories based on multiple criteria like social engineering risks, data leaks, cubit score, vulnerabilities, email spoofing, IP reputation, and DMARC, and phishing. It is a good idea to compare your cybersecurity strategy and KPIs with that of competitors to see what they are doing better.
12. Patching cadence
This cybersecurity performance indicator measures the number of security susceptibilities that are already present in your system and their remedy plans. Further, it is necessary to document the methods by which third-party vendors are being patched and requirements and deadlines are being communicated. In short, this KPI will help evaluate if you recover a service or product failure or simply prevent it altogether.
13. Competitive intelligence
A business must always strive to achieve security measures that are in compliance with relevant industry standards to better protect against cyber attacks. You can start by checking which specific risk mitigation strategies your peers are following to stay ahead. Further, learn the trends and patterns that have emerged over the years and if your business needs to have them implemented. Lastly, try to enforce the best security practices to prevent both insider and outsider threats.
14. Cost per incident
Despite the importance of all the above KPIs, a business must analyze the financial impact of responding to every threat incident. This will include detection, investigation, productivity loss and mitigation expenses. It is also a good way to figure out which areas would require you to strengthen the ‘human elements’ of security defenses.
Choosing the best cybersecurity metrics for business protection
Well, choosing cybersecurity metrics completely depends on your business requirements, the industry you belong to, goals and objectives, and the regulations, practices, and guidelines that need compliance. Further, the risk appetite of your customers is another important factor when picking a cybersecurity strategy.
Lastly, the KPIs must be clear to everyone like employees and stakeholders so you do not have to explain your moves. On your part, ensure you are able to offer at-a-glance visibility to anyone who would require transparency in the cybersecurity process.
Get in touch with cybersecurity professionals like us at Simublade who will conduct round-the-clock supervision to bolster data security.
FAQs
Q. What are the most critical cybersecurity KPIs that every business should monitor?
Ans. The most important cybersecurity KPIs for businesses are preparedness, access management, MMTA, MTTC, MTTD, security compliance, and patching cadence to name a few. It is a good idea to consult a cybersecurity firm like Simublade for a clear picture.
Q. What are the common challenges in measuring cybersecurity KPIs?
Ans. Common challenges include identifying the right metrics, interconnected nature of KPIs that can confuse businesses, and the frequent rise of new KPIs. Outsourcing the cybersecurity services to a trusted cybersecurity company can help you avoid these.
Q. How do cybersecurity KPIs influence overall business strategy?
Ans. Threat detection and solutions can help with customer retention, better revenue and profits, protection of business reputation, and ultimately staying ahead in the competition.
Q. Can small businesses benefit from tracking cybersecurity KPIs?
Ans. The short answer is yes. In fact, small businesses must definitely consider tracking cybersecurity KPIs to avoid major pitfalls or a complete business shutdown. At Simublade, we can tailor strategies exclusively for startups to meet their unique security goals.
Q. How can Simublade help businesses in tracking and optimizing their cybersecurity KPIs?
Ans. At Simublade, our cyber protection experts run an in-depth analysis of network assets and vulnerabilities and use specialized tools to build solutions that maintain an up-to-date infrastructure. We also add multiple layers of protection in the software’s control design to make sure only authorized people are getting access.
Q. How do cybersecurity KPIs help in mitigating risks?
Ans. Cybersecurity metrics and KPIs offer invaluable insights into the security landscape of a business to identify and mitigate threats. Overall, these are essential to minimize data exposure and exploitation.





