Mobile apps are more like personal assistants in our pockets which are indispensable tools adding efficiency and convenience to our daily lives. However, they tend to present critical security issues, which when not addressed promptly, can lead to data exploitation. As per Kaspersky Security Network, 10.1 million attacks by adware, malware, and risky mobile software were blocked in Q1-2024 alone. These harrowing statistics make it extremely important for organizations to ensure their apps are ultra secure to prevent mobile app vulnerabilities that could modify the app’s behavior.
The first step to get started is to learn about the threats in detail to be able to understand and identify the gaps in your app security. This will help businesses plan a proper quality assurance session with experienced developers to release a hack-proof product in the market. Read on to be able to know about common mobile app vulnerabilities and solutions and make informed choices.
Table of contents
Weak encryption
Weak encryption tops the list of mobile app security threats since it exposes highly sensitive data to potential breaches. When encryption algorithms are improperly implemented and outdated or weak keys are used, attackers easily decrypt confidential information such as:
- user credentials
- payment details
- personal data
This weakness is specifically quite concerning for fintech and banking apps that handle regular financial transactions or store private information.
Solution: Avoiding this mobile app security risk is easy since the best developers typically use strong, up-to-date encryption standards like AES – 256 which helps with end-to-end encryption for data transmission along with closely managing encryption keys. Additionally, cybersecurity measures like regular testing and security audits for encryption flaws are critical to maintain robust app security.
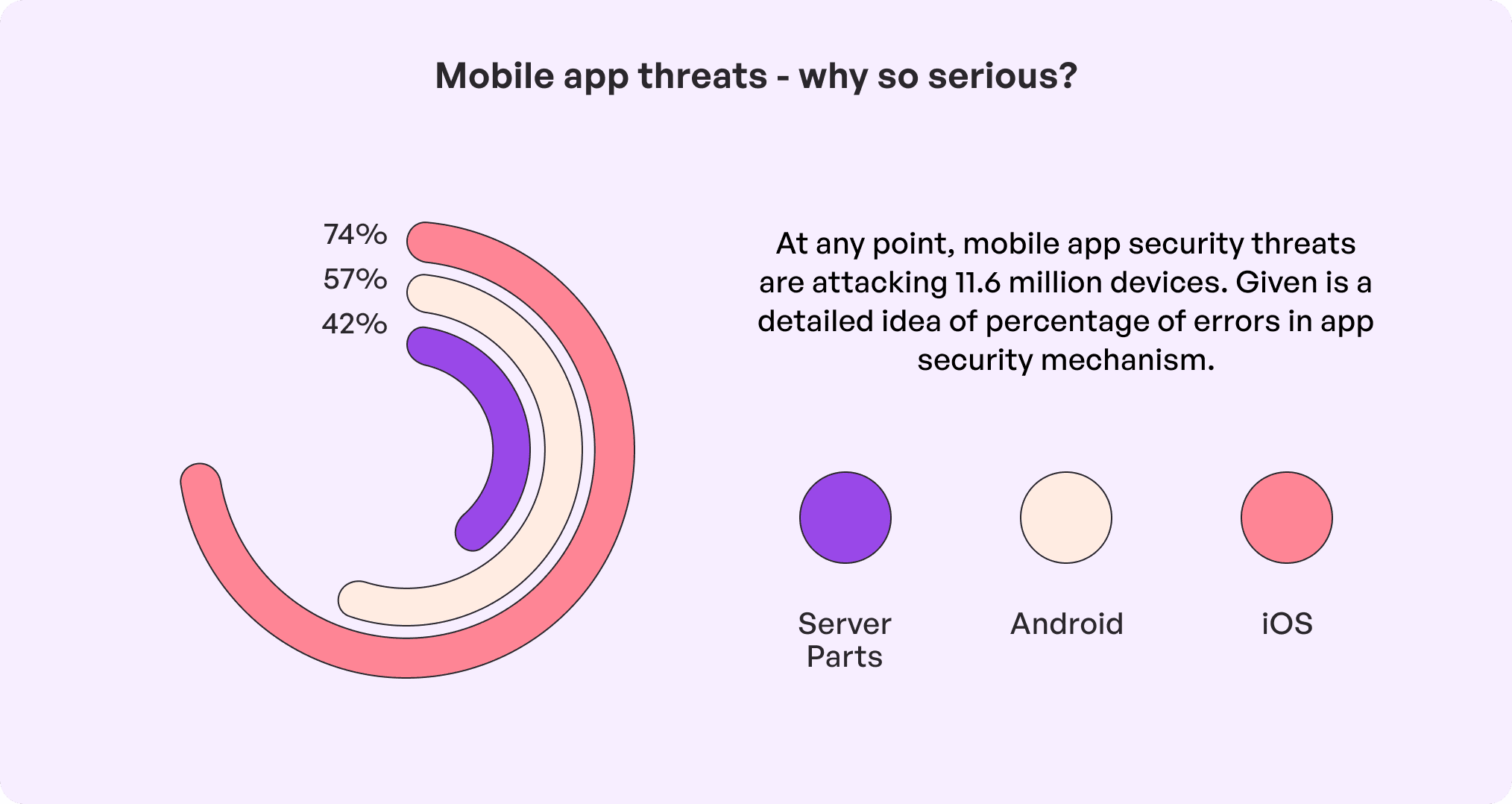
Injection flaw
This is when hackers can relay information via an application into a system. The process is done by ‘injecting’ and running harmful codes into the mobile app when the user unknowingly inputs data into an interpreter. This causes the app to overlook data sanitization like in SQL, LADP, and OS command injections which leads to unauthorized data access or even a full system compromise. This ultimately hampers app functionality and user trust.
Solution: To stop or reduce such malicious exploits, developers add parameterized queries, use language-specific libraries, deploy WAFs, check error codes from calls, apply least privilege, avoid external interpreters, escape special characters, and input validation. Further, they also ensure using stored procedures and safe APIs.
Malware attacks
Studies have found that approximately 1.2 billion malicious programs and potentially harmful applications exist today which are rapidly increasing with time. These pose significant vulnerability thus exploiting weak security to steal confidential data and ultimately infect devices and hinder customer trust. The attacks generally occur through malicious apps that are highly disguised as legitimate ones or via compromised updates.
Once they are installed, malware could access personal data, banking credentials, or even take control of the whole device. Poorly encrypted data, insecure API connections, or inadequate permission settings can further increase an app’s susceptibility to such threats.
Solution: Experienced developers implement strong security protocols like encryption, adhering to strict app store guidelines and regular security audits while users must be made cautious against app downloads from unknown sources.
Code tampering
This refers to the unauthorized modification of apps’ codes when it has been deployed. Code tampering is common if attackers manipulate the source code, libraries of an application to alter its behavior, and binaries for malicious purposes. Tampered code will lead to vulnerabilities like injected malware, allowing attackers to bypass security checks, stolen sensitive data, or changed app key functions of the app, for instance, like in-game currency in gaming applications. The most common methods of code tampering are altering APK or IPA files, injecting malicious code into the app and reverse engineering the app to understand its code structure.
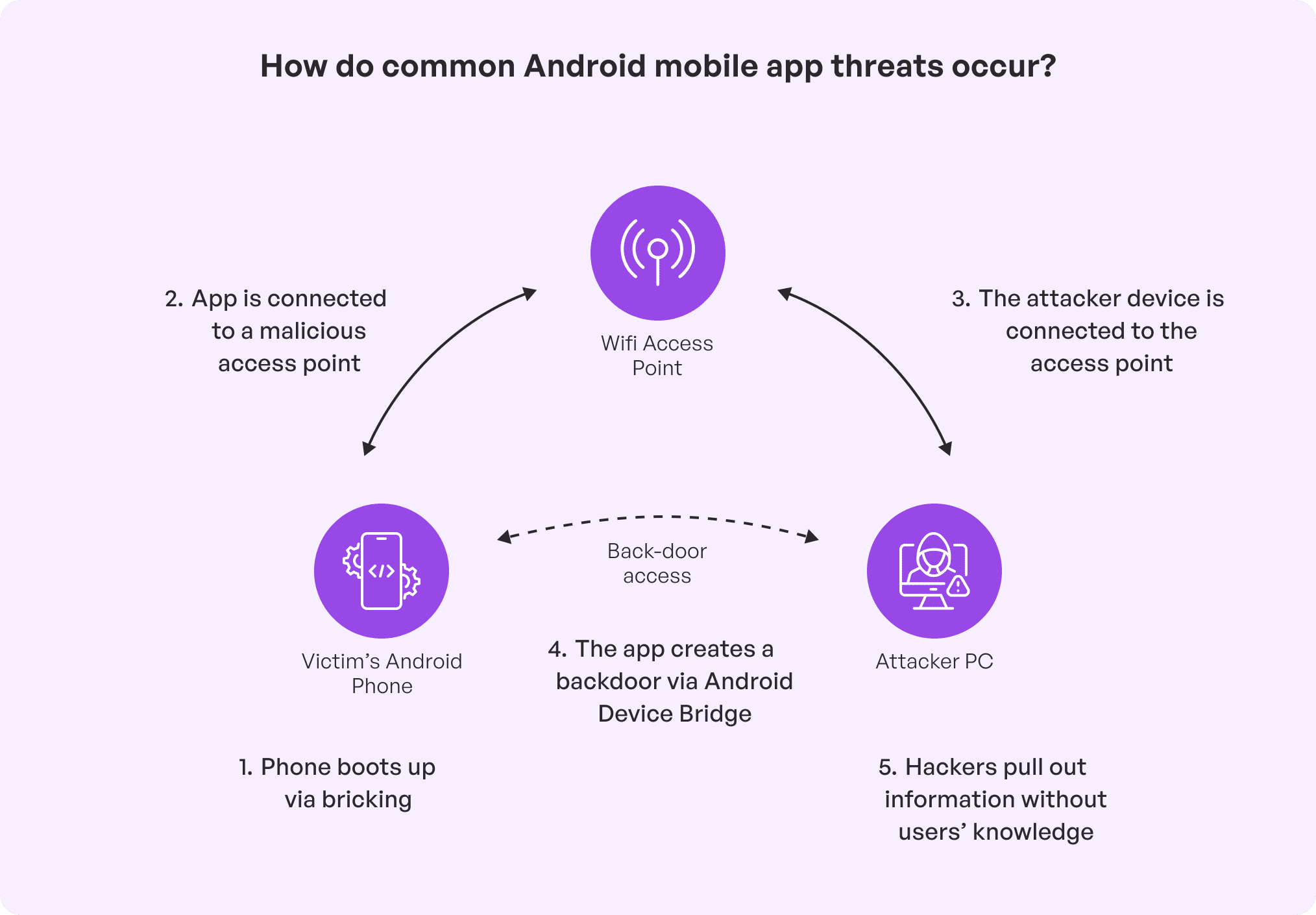 Solution: To protect against this common mobile app security threat, developers conduct integrity checks, code obfuscation, digital signatures, and runtime application self-protection (RASP) to detect and respond to unauthorized changes in real time.
Solution: To protect against this common mobile app security threat, developers conduct integrity checks, code obfuscation, digital signatures, and runtime application self-protection (RASP) to detect and respond to unauthorized changes in real time.
Minimal binary protection
Minimal binary protection is one of the top mobile app vulnerabilities where the application’s binary code, which is basically the app’s compiled version, lacks strong security measures. This way, it becomes easy for hackers to tamper-with, reverse-engineer, or make changes to the app. Not having robust protection can help attackers decompile the code easily to uncover confidential data like:
- business logic
- API keys
- cryptographic algorithms
This ultimately can lead to data breaches, code tampering, or malicious code injection. The worst scenario is that even the most popular apps with strong protection fall prey to these mobile app security risks.
Solution: To mitigate this, developers should implement code obfuscation, encryption of sensitive data, and integrity checks to prevent reverse-engineering and unauthorized modifications. Additionally, runtime application self-protection (RASP) is used to detect and respond to tampering attempts while the app is running.
Weak authorization
It is an insufficient or non-proper access control that allows unauthorized users to bypass the confidential or restricted data of an app. These kinds of mobile app vulnerabilities can lead to breached privacy and compromised accounts. A few ways to identify weak authorization include weak passwords, unverified user identity, and suspicious requests.
Solution: Developers typically avoid using spoofable values like device or location to authenticate a user. Instead, a 4-PIN authentication would be quite a smart move. Further, multi-factor authentication, disabled username enumeration, modifying cookie headers, single sign-on, HTTP strict transport security (HSTS), and brute force protection are extremely helpful to avoid protecting an app.
Reverse engineering
This process breaks down app files by analyzing and decompiling which helps hackers get into the core of its functionality, structure, and security gaps. They analyze the weaknesses like insecure APIs, authentication flaws, and hardcoded keys that could be exploited and do so which ultimately crashes the app.
Solution: What developers typically do is analyze an app’s binary or code to identify security flaws. By deconstructing the app’s logic and flow, developers are able to pick weaknesses, such as incorrect encryption and insecure APIs, and then develop fixes and patches. This is a highly efficient process and ensures that vulnerabilities are accurately addressed and long-term exploits are prevented.
Vulnerable OSS
It is a security gap in any open source software that is exploited by hackers for unauthorized access to a network or system. It happens due to public accessibility which was previously considered excellent for improvement but on the other side of the coin lies threats due to increasing mobile app security vulnerabilities. This includes outdated libraries, lack of visibility, insufficient maintenance, misconfigurations, and insecure dependencies.
Solution: The simplest solution is to automate the entire process or opting for an open-source vulnerability scanning tool like SCA. It will help with quick identification and mitigation. Further, developers typically adhere to the best standards, licenses, and practices of open-source to be able to dodge such mobile app security vulnerabilities.
Knowing how to avoid security risks in mobile apps is critical since more than 75% of all published apps typically have at least one vulnerability or other in them. So, while there is a specific solution for each one, there are a few common solutions that every developer usually follows. Having a fair idea helps businesses plan the app security too. Here’s a look.
Simple steps to reduce mobile app security threats
Below are the best practices to prevent mobile app vulnerabilities ensure minimal or even zero vulnerabilities in mobile app development:
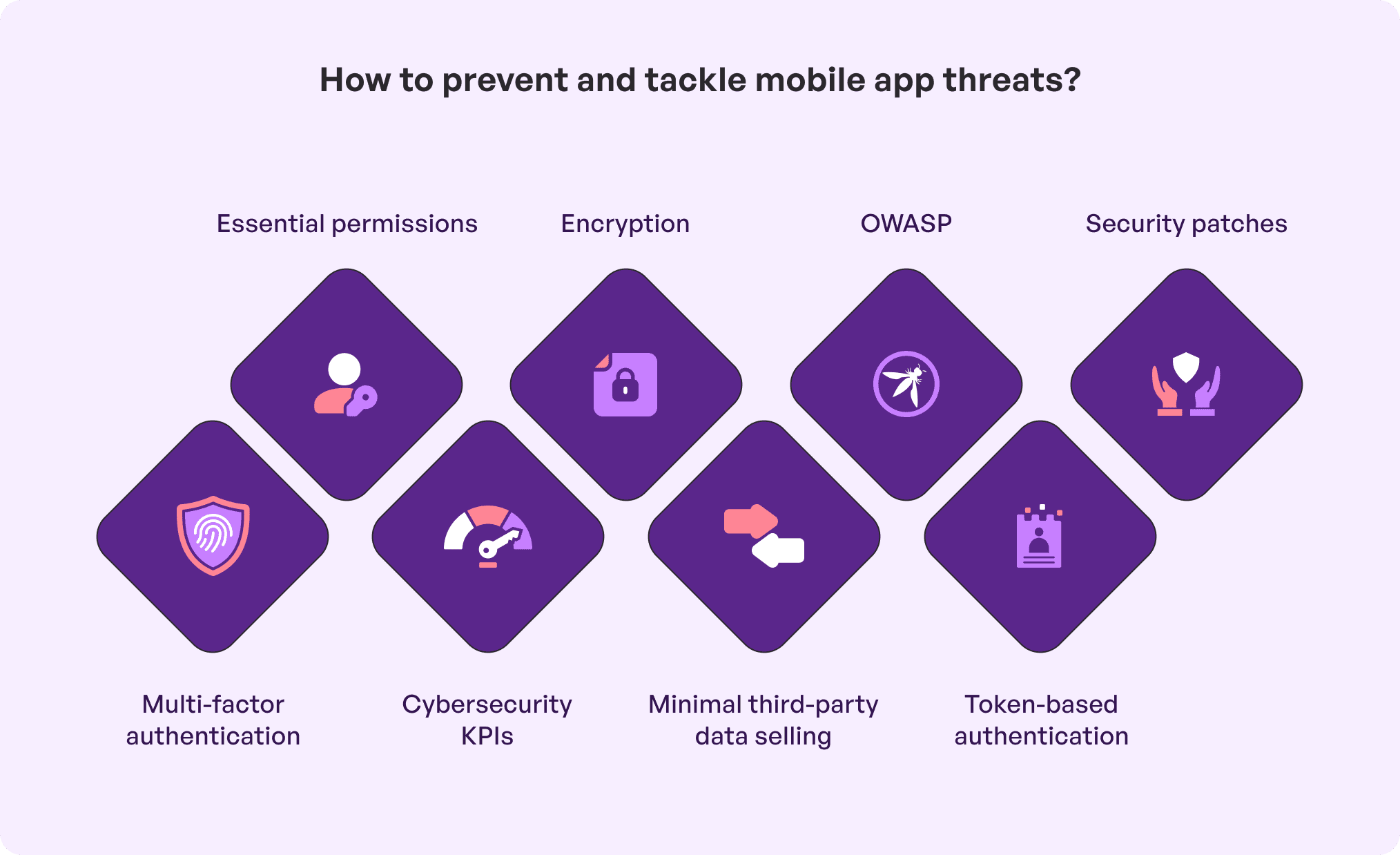
- Using multi-factor authentication (MFA) and stronger-than-usual password policies to make sure the user accounts of your customers are safeguarded.
- Abide by OWASP which is a mobile app security framework to identify and remove risks especially from applications.
- Encrypt all sensitive data of your business (finances) and customers (private information). This must be done both in rest and in transit to prevent unauthorized intervention or illegal access.
- Avoid selling data to social platforms like Facebook without user permission. This could lead to breach of reliability and user privacy along with malicious attacks. For instance, Flo app in 2019 had deliberately sold data to giants like Facebook and Google without permission and the consequences were quite unpleasant. However, if you have to do so at all, consider limiting the way these platforms can use the information to avoid breaking user trust.
- Try to request only essential permissions like photos and location for the app instead of irrelevant details like call logs or media files to function. Otherwise, seeking unnecessary permissions is likely to expose users to privacy risks.
- Your app must follow all cybersecurity KPIs which helps plan a mechanism in place to identify non-human traffic and validate user inputs. This is a fast and important way to buffer overflow vulnerabilities and bypass attacks like SQL injection.
- Apps and third-party libraries must be kept up to date with security patches to protect against potential security loopholes.
- Data encryption and token-based authentication are safe ways to avoid API misuse and exposure.
Opt for rigorous QA and software testing from trusted companies to be able to enjoy the most comprehensive protection possible in your applications. This is where we at Simublade can help by offering quality assurance services to ensure hack-proof digital solutions with security testing and system testing. We also provide a ‘plan and fix’ strategy where our experts close gaps in existing apps and determine security metrics and parameters for the future.
Conclusion
While of course mobile app security threats could interfere with business operations, the positive side is that they are an opportunity to stay up-to-date with security innovations. Owing to this, you must explore proactive regulatory frameworks by partnering with companies like Simublade to ensure your apps are highly resilient to threats. Further, ethical practices, user privacy, and transparency in app policies are a must to be able to ensure a risk-free experience and ultimately stay ahead of competitors.
FAQs
Q. What are common security risks associated with mobile applications?
Ans. Common mobile app security vulnerabilities include reverse engineering, weak authorization, weak encryption, and minimal binary protection to name a few.
Q. How does insecure data storage affect mobile apps?
Ans. Insecure data storage leads to leakage, privacy violation, improper app usage, and overall reputation damage. The best way to understand mobile app vulnerabilities and solutions is to get in touch with trusted QA companies like Simublade.
Q. What are some best practices to avoid mobile app vulnerabilities?
Ans. The best practices to prevent mobile app vulnerabilities include strong encryption, robust passwords, multi-factor authentication, and regular integrity checks.
Q. How can developers ensure secure communication in mobile apps?
Ans. Encryption and authentication in mobile apps are the best ways to ensure secure communication.
Q. What are the risks of poor authentication practices in mobile apps?
Ans. The risks are numerous including code tampering, identity theft, data leakage, and malware which impacts technicalities and overall business functions.
Q. What is OWASP’s role in mobile app security?
Ans. The OWASP Mobile Application Security Verification Standard (MASVS) is an industry standard for app security which ensures testing mobile applications for security vulnerabilities. The process will include detecting, assessing, and addressing threats as per individual degrees.
Q. What is a common factor that contributes to mobile app security threats?
Ans. Insufficient cryptography, unsecured Wi-Fi, and improper session handling are common factors for mobile app security risks.